
The LinedIn hack was a big catastrophy not only to LinkedIn. Since the site failed to salt their passwords, all weak passwords must be considered compromised.
Check if your email address was in the leak: LinkedIn LeakChecker
What does the hack mean for Austrians and their passwords?
Hard facts
- There were
105.386accounts with an email address that ended in .at - In the datadump there were
76.344sha1-hashed passwords from those accounts 42.980(67%) of these passwords can be cracked in under 1 hour on consumer hardware1.011accounts were government accounts (ending with gv.at). This includes military13.239of the compromised accounts were GMX addresses- LinkedIn didn’t salt the passwords. This fact makes this leak much more dangerous
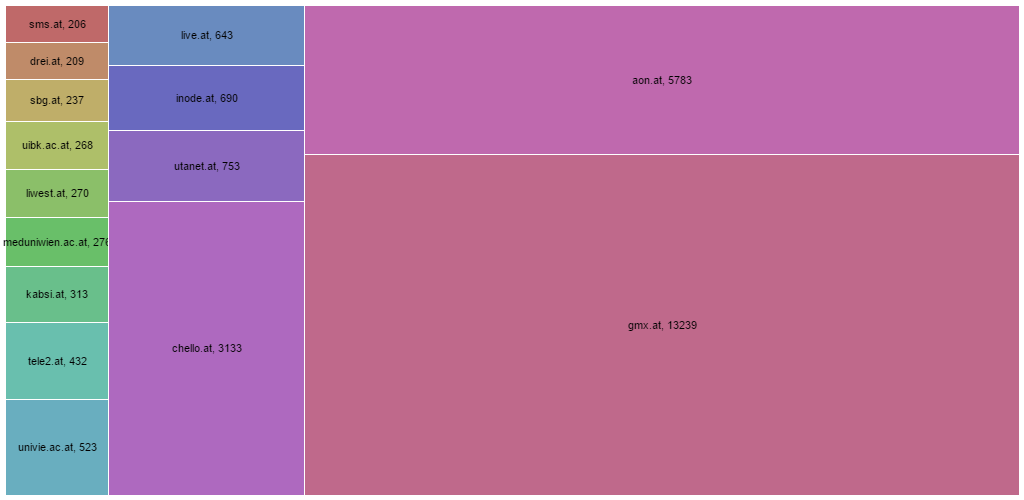
Where do these accounts come from?
When we look at the email providers we can see GMX as the most common provider for people with weak passwords with 13239 accounts.
Let’s look a little closer at the passwords
These (partial) words and numbers are in most passwords
In detail here the most common passwords and how many times they were found in the leak. Be aware that these are just from the 42.000 weak passwords in the database. The real good passwords don’t show up here.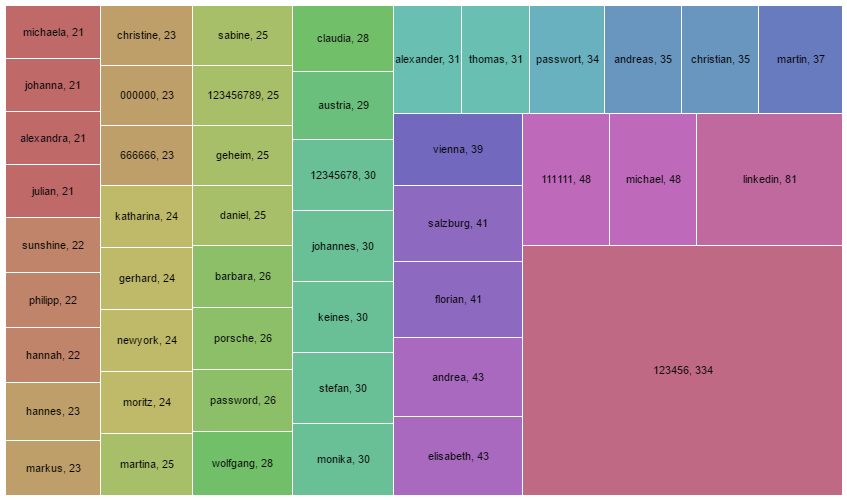
So the most used passwords were:
- 123456
- michael
- 111111
The most common passwords by austrian accounts as a round dendrogram.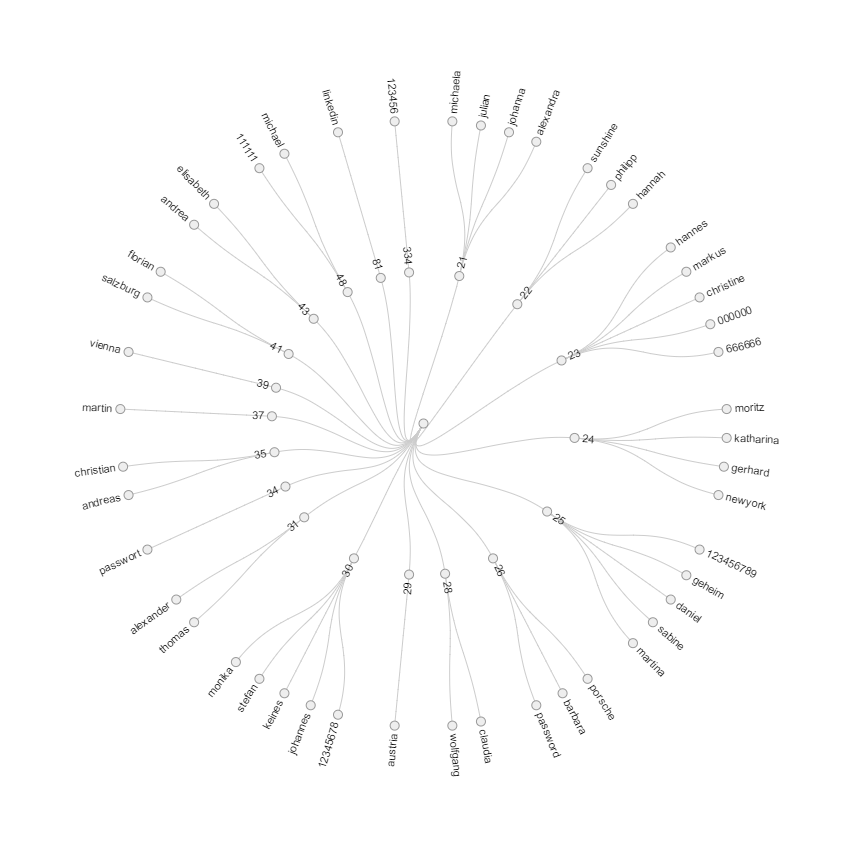
Where do we go from here
Since 67% of the analyzed passwords can be considered as weak passwords we have to ask ourselves what are good passwords.
According to Edward Snowden, phrases are good passwords:
Or you can make the XKCD approach: